Category: Security & Privacy
-

SQL Template for Managing GDPR-Sensitive Data in Databases
Managing GDPR-sensitive data requires marking fields, ensuring proper retention, and setting up automated deletion processes. Below is an extended SQL template with typical fields that could exist in a database, helping you build in Security by Design and GDPR compliance from the start. SQL Template for GDPR Compliance: Key Points: This template can be adapted…
-

The Business Value of Implementing GDPR-Sensitive Data Management in Databases
In today’s data-driven world, compliance with regulations like the GDPR is not just a legal requirement – it’s a competitive advantage. Businesses that integrate GDPR-sensitive data management directly into their databases are building trust, reducing risks, and creating operational efficiencies that drive long-term value. Key Business Benefits of Implementing GDPR-Sensitive Data Management in Databases 1.…
-

Build a Disaster Management Hub with a Raspberry Pi
– Featuring Sahana Eden – When disaster strikes, the ability to manage critical information and provide localized support can mean the difference between chaos and organized response. As no disaster is announced in advance, the necessary equipment for disaster management will not be present from the first second. This article is intended for communities, private…
-

Investment Opportunities in European Tech: Reducing Dependency on U.S. and China
In today’s rapidly evolving tech landscape, global dominance by U.S. and Chinese tech giants presents both challenges and unique opportunities. For investors looking to support the rise of European alternatives, there is significant potential to capitalize on growing demand for privacy-focused and independent digital services. Search Engines: Qwant, Ecosia, and Startpage – Opportunities for Growth…
-

Boosting Website Analytics While Respecting GDPR
– A Guide for Privacy-Conscious Website Owners – In today’s data-driven world, website analytics are crucial for understanding user behavior, optimizing user experience, and making informed decisions. However, with the European General Data Protection Regulation (GDPR) in place, website owners need to ensure that their data collection methods are compliant, secure, and respectful of users’…
-

Organizing Decentralized Emergency Communication with Ham Radio and Open-Source Tools
In an age where natural disasters, infrastructure failures, and geopolitical tensions can disrupt normal communications, communities need resilient and decentralized systems to stay connected. One of the most powerful yet overlooked resources in this context is amateur radio – combined with open-source crisis management platforms like Sahana Eden. Why Ham Radio Still Matters Ham radio…
-

Dynamic web content from US web services is illegal in Germany
The integration of dynamic web content such as Google Fonts from US web services is illegal in Germany without the visitors’ consent. This was decided by the Munich Regional Court in a judgement (Ref. 3 O 17493/20). Website operators can be sued for injunctive relief and damages. Although the ruling of the Munich Regional Court…
-
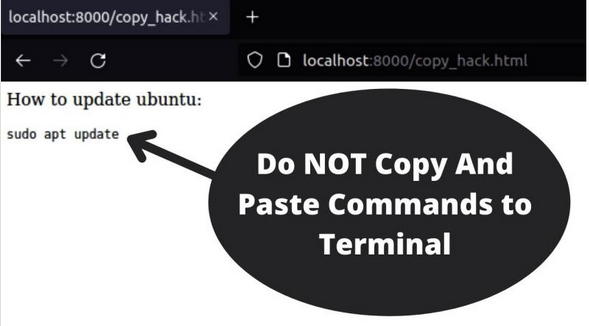
Don’t copy-paste commands to terminal
Reasons not to copy-paste between a web page and your terminal. Evaluate the copied in your simple text editor before hand. And don’t use Microsoft Word for this. Video: NOTE: The use of YouTube will send data from you outside of Europe. https://youtu.be/LFXZqQL4vTY #security #securityawareness #windows #linux #linuxserver #linuxsystemadministration #sysadmin #sysadmins
-

Google Play app with 500,000 downloads sent user contacts to Russian server
Yes, “of course” are Google Play Store apps secure. Google Android tells you that anything else isn’t when you try to use another app store. https://arstechnica.com/information-technology/2021/12/google-removes-malicious-app-that-infected-500000-google-play-users/
